Theft of Service-Inevitable?
December 2005 Issue
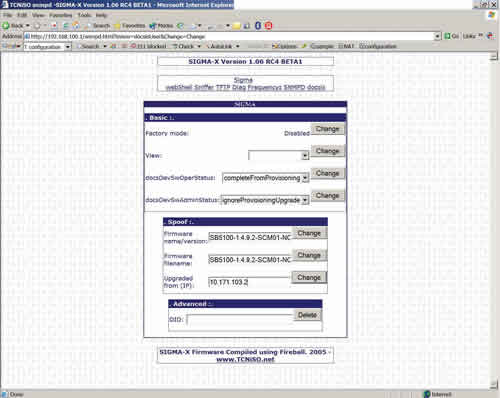
Data service theft is on the rise and getting easier every day. But it can be checked-often via things you should already be doing. By Mark Millet, Cisco Systems Broadcast cable TV theft of service has long been a nebulous area-there is lost revenue, but if those customers are going to end up in collections, sometimes it is cheaper to simply ignore them and the service costs associated with the account. There is no operational expense to this lost signal-at least until there is so much theft that a premium network says it will pull the franchise or raise rates. Cable modem service is a completely different animal-theft occurs in two modes, stolen service and upgraded service. There are nearly 15,000 known "pirated" cable modems today and more than 500 percent annual growth. A significant difference between "proprietary" set-top boxes and DOCSIS modems is the retail factor. Thirty-nine dollars buys a box that can be converted in 15 minutes following videos and instructions available on the Internet. A customer may keep the "real modem" as a decoy and also use a modified modem for criminal activities. Cable modem service theft has direct costs to the cable operator: lower throughput available to paying customers, denied access because of modem cloning, and a little known indirect cost-the cable operator’s liability to identify the source of malicious attacks entering the Internet. Internet crime is serious business-law enforcement personnel will break down the door in full battle gear under the right circumstances. Tools are available There is very good news about cable modem security and theft: A plethora of tools used with automated monitoring can already eliminate all known methods of theft of service. Several operators are successfully using these tools and are down to minor nuisance issues. Cable modem termination system (CMTS) vendors are assisting with DOCSIS 3.0 specifications development and also the operations side to deal with today’s installed base. DOCSIS security can be broken down into a few short requirements: 1. An online cable modem must use the service profile assigned by the provisioning system at the time it comes online. 2. Real-time detection and control for cloned cable modems. 3. Verify that an online modem is not modified or behaving in an unusual manner and is running the expected software, including checks to verify that the reported software version is the actual software version. Once the cable operator’s network performs all of these tasks, there is no longer a theft of service problem. Specific methods The most direct and effective method to implement No. 1 is to make the DOCSIS configuration file valid for a single use only and only for the assigned cable modem. Thus, the days of the static configuration file are gone. Either the provisioning system or the CMTS can make the dynamic file for each registration request. One way to improve anti-theft technology is by moving the DOCSIS trust model away from the cable modem and to the CMTS. The CMTS monitors the provisioning process, obtains the DOCSIS config file on behalf of the modem, and inserts a onetime password and cryptographic signature into each file’s CMTS MIC, or message integrity check field. By changing the dynamic host configuration protocol (DHCP) offer to point to the CMTS, it only allows the modem to register if the onetime CMTS MIC matches and hides the insecure trivial file transfer protocol (TFTP) server from the network. This feature is called, "cable dynamic-secret," or DMIC for short. DOCSIS 3.0 will mandate a form of DMIC. Dynamic provisioning systems can place the requesting device’s Internet protocol (IP) address and a timestamp inside the file. This makes files nontransferable and prevents reuse, but does not protect against the latest "Sigma-X" features from the www.tcniso.net Web site unless used with "cable source-verify DHCP." The modified modem will simply choose the IP address of a device the miscreant user wishes to impersonate and ignore the address assigned by provisioning. As a result of these effective security techniques-and the now defunct and insecure "TFTP-enforce"-miscreants have resorted to device cloning. By December 1986, cloned cell phones were costing operators $1-2 million per day. (See http://www.cnn.com/TECH/9612/10/cellular.cloning/ and http://www.cnn.com/TECH/9704/15/cellphone/ for more information.) The long-term solution was global roaming, which instantly checked if a phone came online in two different locations at once, shutting down either both units or only the identified clone. Short-term attempts to fingerprint legitimate devices have all been abandoned as technology rapidly made these obsolete and too costly. It is trivial to create a poor clone of a cable modem and somewhat more challenging to create a perfect clone. The poor clones are made by listening to modems coming online (DHCP offer) and simply inserting a different media access control (MAC) address into a modem. Sigma-X does this on the modem itself and presents that data on a Web page. These are easily defeated by enabling Baseline Privacy Interface Plus (BPI+) in DOCSIS 1.1 deployments. Perfect clone modems are made by copying all the information inside the cable modem. Forty dollars for the TCNISO Blackcat software and cable and 15 minutes’ physical access with a laptop computer will capture everything necessary. Such modems may show up on a different CMTS and operate for weeks or months unnoticed. The key to clone prevention is immediately denying service. If the modem cannot be made to operate for more than 2 minutes out of every 24 hours, cloning is useless to the miscreants. If the modem operates fine for 12 hours at a time, clones "work just fine," and there are "plenty more MAC addresses out there to clone." It may be best to simply not issue IP addresses to detected clone modems, since the settings of a disabled config file are already being ignored. The more worrisome threat is cloning across the hybrid fiber/coax (HFC) network itself. In this case, the miscreant uses simple network management protocol (SNMP) to force the victim’s modem to download a modified image that sends the necessary private key data across the HFC network. Even though there is no business or revenue justification, most operators neglect to implement simple CMTS access lists preventing all modem-to-modem communication and PC-to-modem (through the CMTS) communications. One major operator chose to rely solely upon the cable modems for this task and became mired in model- and version-specific capabilities, bugs and device limitations. They became experts in which DOCSIS certification wave each model passed because the contents necessary in the DOCSIS config file change. The miscreants have already disabled modem access lists, and this only stops those who have not yet purchased serial or TCNISO interfaces for their modems. Regarding No. 3, when a cable modem connects to the CMTS, the CMTS maintains a record of the modem, its class of service and traffic statistics. A simple sanity check against the CMTS looking for expected modem information and flagging failures or irregularities will provide untold benefits. Modems operating normally will match provisioning; other modems will often have conflicting responses between the CMTS, modem and provisioning. Miscreant cable modem code is showing some information about unsolicited grant service (UGS) flows. These and other dynamic service flows send high priority traffic for voice or PacketCable Multimedia (PCMM). Unfortunately, the DOCSIS and PacketCable standards assume a modem will never ask for something it doesn’t legitimately require. The solution is a simple type/length/value (TLV) in the DOCSIS config file for any modem that has no business need for these flows. (See sidebar above left.) If the DOCSIS 1.1 cable modem with BPI+ does not authenticate properly (poor clone), the CMTS prevents it from registering and logs its MAC address and authentication status in the docsBpi2CmtsAuthTable management information base (MIB). The CMTS may also be configured to deny certain MAC addresses that pass BPI+ (perfect clones) from registering using the docsBpi2CmtsProvisionedCmCertTable MIB. This table overrides the normal BPI+ authentication function. A normal cable modem will respond to SNMP queries, and some of those queries will result in errors or invalid results. Others should show traffic flow matching the results of the CMTS. Suspicious cable modems need extensive SNMP interrogation to determine a fault and will evolve to provide the expected responses. Today, a Sigma-X cable modem will falsely indicate it contains the expected firmware version and was successfully updated by the cable operator’s server. The face of theft Tables 1 and 2 summarize output from hacked modems in both insecure and secure networks. 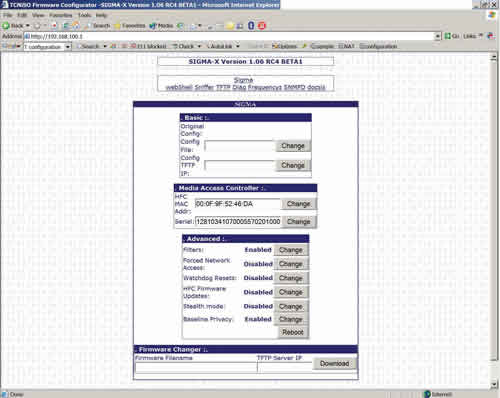
 In a secure network, the CMTS provides all provisioning information, cable dynamic-secret is active, and the DHCP server is setting giaddr-as-server-id, such that no device can spoof the option-82 data. No traffic can pass from the cable modem to or from any IP address other than an SNMP management station or cable modem code upgrade server (outside the 10 network) or the router IP address. Clones are detected in real time, and no IP address is issued to clone modems, or the modem is given a config file with very low throughput, or access to a special "walled garden" notifying the user they are being monitored for malicious activities. So although the miscreants are becoming increasingly tech-savvy, theft of service is by no means inevitable. Reasonable awareness and precautions on the operator’s part (many of which you should already be doing anyway) will hold data service theft to a minimum. Mark Millet is a technical leader, Security and System Test, for Cisco Systems. Reach him at mmillet@cisco.com.
In a secure network, the CMTS provides all provisioning information, cable dynamic-secret is active, and the DHCP server is setting giaddr-as-server-id, such that no device can spoof the option-82 data. No traffic can pass from the cable modem to or from any IP address other than an SNMP management station or cable modem code upgrade server (outside the 10 network) or the router IP address. Clones are detected in real time, and no IP address is issued to clone modems, or the modem is given a config file with very low throughput, or access to a special "walled garden" notifying the user they are being monitored for malicious activities. So although the miscreants are becoming increasingly tech-savvy, theft of service is by no means inevitable. Reasonable awareness and precautions on the operator’s part (many of which you should already be doing anyway) will hold data service theft to a minimum. Mark Millet is a technical leader, Security and System Test, for Cisco Systems. Reach him at mmillet@cisco.com.