Cyber Safety
Secured Messaging = A Protected Brand
Cyber threats against most organizations, including cable providers, increasingly are originating from emerging countries where Internet infrastructures are growing rapidly. Attacks—including phishing, bots, spam and denial of service (DOS) attacks—from these developing areas are becoming more malicious in nature and can be directed at any country. Where previously attackers wrote a relatively small number of threats targeted to a large group, now they create a much higher number of threats targeted to small groups.
As a hedge, cable providers now need to implement a progressive solution that is global in its resources and blends automation with human intelligence. Increasing, barriers to unwanted attacks not only will save the company money, but also will help protect the company’s brand reputation by enabling a better user experience.
Only a next-generation threat-protection system that enables the dynamic application of real-time intelligence sharing for greater effectiveness, responsiveness and operational efficiency can absorb and defend against these sophisticated attacks. Cable operators need a multi-tiered system that provides protection at both the network and application levels to enhance the accuracy and effectiveness of threat detection and ensure the environment remains safe.
With a sweeping approach to message security that goes beyond content scanning, carriers and other service providers will gain a competitive edge through improved service levels and better user experiences. That means less customer churn, higher average revenue per user (ARPU) and simplified management—all at a lower total cost of ownership.
Email remains a vital messaging channel for cable providers. However, spam continues to grow (now 85 percent of all email traffic) and evolve along with the increasing number of such security threats as viruses, phishing (see Figure 1 and Figure 2 on page 24), Trojan horses and malware. More than 40 percent of IT groups cite cyber risk as their top concern, yet most carriers continue to rely on technology that’s a step behind. Failing to detect these threats early and allowing them to infiltrate the network deeply is costly. In addition to hard costs, cable providers face customer-satisfaction issues that often are damaged beyond repair.
Almost No One Is Immune
If last year is any indication, three out of four communications service providers will be hit by cyber attacks in 2010. While the potential damage from these and other attacks, such as DOS, can be severe, fully 90 percent are avoidable if companies better protect their networks. Unfortunately, operating budgets for messaging security continue to be under pressure even as volumes and threats grow.
As such, messaging threats tend to be treated with older solutions using historic thought practices and pieced-together disparate products and services. Solutions that offer advanced message management and security capabilities in a single integrated package simply have not been available until recently. The net result of these factors generally is sub-par threat protection.
Key Components
In some cases, cable providers are strapped by legacy systems that aren’t flexible and don’t scale. In others, they’ve got point applications and platforms that aren’t extensible or simply don’t provide solutions adequate to today’s challenges and needs. What’s needed is a combination of best-of-breed products and services to create a well-rounded suite of message security and management solutions. This combination will more readily enable service providers to achieve their business objectives, to post higher financial returns and to gain a competitive edge in the marketplace.
Cable providers should look for features that include network-level, multi-tiered filtering; advanced spam detection and prevention capabilities; flexibility in running different rule sets for different groups on a side-by-side, per-message basis; and the unparalleled ability to integrate into virtually any client environment.
To keep the network and customers safe, cable providers need a next-gen threat protection system that stays ahead of threats and helps ensure airtight security in an ever-changing environment. This solution requires a comprehensive, holistic approach that enables carriers and service providers to block threats at the earliest point with fully integrated security components at all levels (content, protocol and edge of network) for realtime intelligence sharing.
As a result, they can detect and respond to threats faster (before they cause serious damage to the business), deploy enhanced security capabilities to counter ever-evolving attacks, improve service levels, improve customer experiences and reduce costs through streamlined operations.
An important consideration for cablecos regarding a next-gen threat protection system is tight integration offered by independent application and platform providers. Tight integration is important to maximizing the benefit of both, but not to the point of restricting choice, such as with a single-source or closed solution. Choosing independent application and platform providers is important because it allows cable providers to take advantage of the technology innovation of both while preserving the choice to respond to ever-changing threats in the ways that best suit each operator’s unique needs.
The Benefits
Here’s a comprehensive checklist regarding the benefits of an integrated solution:
It provides better service: The need for cable providers to enhance the user experience, and to reduce customer churn and infrastructure investment is not a “nice to have;” it’s a “must have.” Genesys, Greenfield Online and analysts from Datamonitor/Ovum found a $50.6 billion loss from customer churn and industry defects. Cable providers are fighting to keep customers who are looking at low cost and free services. Estimates show the cable/satellite industry has lost more than $10 billion from poor customer service.
It better leverages existing infrastructure: The cable industry can better leverage its infrastructure by stopping spam at the network level. However, efficiency and effectiveness gains are based on intelligence-sharing between all components of a solution. This means the solution is dependent on adequate end-to-end resources to identify abuse and to communicate (share intelligence) with the other components. While lower overall network traffic might appear to justify a reduction in downstream servers, such reductions could hinder the effectiveness of the solution and could introduce latency. With the cable industry looking to expand into the business/enterprise market, operators should leverage their existing infrastructure but take caution in reducing it.
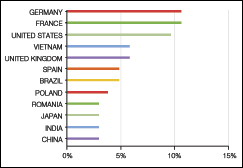 |
| FIGURE 1: Phishing Sources by Country. This chart measures phishing by country of origin as a percentage of all phishing email (accurate as of May 31, 2010). Source: M86 Security |
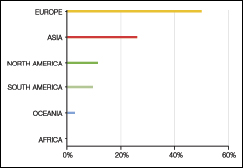 |
| FIGURE 2: Phishing Sources by Continent. This chart measures phishing by continent as a percentage of all phishing email. Europe is the dominant source of phishing emails (accurate as of May 31, 2010).Source: M86 Security |
It provides better decision-making through shared intelligence from other networks and data sources: If a cable provider chooses an intelligence network with a large base of experts and a high detection rate with few false positives, then it most likely find an automatic and seamless information transfer to both internal and external data repositories and additional intelligence that improves a solution’s accuracy and effectiveness in filtering out threats.
It offers complete control and visibility of all messaging activity and response to observed behavior: Unlike point-focused products, multi-tiered systems provide protection at both the network level and at the application level to enhance the accuracy and effectiveness of threat detection and to help ensure the environment remains safe. And with a sweeping approach to message security that goes way beyond content scanning, service providers will gain a competitive edge through improved service levels and better end-user experiences.
There could be lower costs and greater efficiency via connection/bandwidth management: Connection/bandwidth management with SMTP trending and Layer Three network-level control combine multiple content scanning modules with heuristics and reputation data at the platform and network levels for true multi-tiered filtering. Achieved through tight integration, this approach is proved to deliver better results and more efficient operations than specialized point products.
Combined global and local reputation data maximizes accuracy and minimizes false positives with expanded use of a vendor’s reputation lists as well as data from a provider’s local servers. This balanced approach incorporates new feedback faster, further optimizes Layer Three (TCP/IP) throttling at the network edge and blends the benefits of a global view with filtering tailored for your environment. The result is threats are quickly and efficiently identified and dealt with, and spammers seek out more vulnerable targets.
There could be advanced security capabilities to counter ever-evolving threats: Message parking for zero-hour and outbound attacks improves the ability to filter newly released spam threats as well as outbound attacks (egress spam) accurately. Combined with such powerful heuristics as improved botnet detection, fully integrated message parking is an effective method for staying a step ahead of spammers by identifying suspicious messages and holding them for scanning when new filters are available.
Enhanced detection of “snowshoe” spam goes beyond basic filtering methods that aren’t enough to protect from today’s more sophisticated messaging abuse. However, new tools enable the solution to identify snowshoe attacks—small volumes of spam sent from numerous IP addresses—and prevent these covert threats from impacting a network.
Simplified management and solid business continuity: Once a global team is on the same page, it can create a unified interface with robust reporting in a single, unified management console for policy and configuration changes, making administering the solution easy and efficient, and giving cable providers greater control over all parts of email security. Powerful reporting consolidates data from all solution components into cohesive graphs, reports and logs for complete end-to-end insight that’s truly actionable.
Additional components include a streamlined and rapid installation able to duplicate a cable provider’s current configuration so it can be assured of a non-disruptive migration. With the flexibility to run entirely different rule sets for individual user groups on a side-by-side, per-message basis, administrators have incredible control over the way messages are handled across the network.
Seamless integration and carrier-grade availability provide an unparalleled ability to integrate with virtually any environment, resulting in a fast, easy implementation with minimal administration so cable providers can experience the benefits immediately. Some solutions provide an automatic failover to help ensure 100-percent platform availability. Once it’s up, it stays up.
David Harvey is vice president/Business Development at Message Systems, and Ken Schneider is CTO/Enterprise Security Group at Symantec.